Typical Wi-Fi attacks
Last time we presented the main characteristics of the 802.11 standard, often simply referred to as Wi-Fi. This time we want to discuss specific security weaknesses and problems of Wi-Fi networks by presenting typical attack scenarios. This background knowledge will be useful when we will talk about the security of industrial WLAN in our following blog posts.
We will categorize the attacks into three types. There are attacks on the encryption, these are arguably the ones that get most media attention anytime a major issue was found. Another attack type are all kinds of Machine-in-the-Middle attacks that aim at getting information or manipulating traffic by impersonating a legitimate Access Point. The third attack type are availibility attacks that are ranging between annoyance and desastrous effects depending on how important connection to the network is.
Attacks on Encryption
A great amount of research has been done on attacks on the encryption of 802.11 networks. When the standard was introduced in 1997 the Wired Equivalent Privacy (WEP) method was proposed to protect wireless communication. As the name suggests the aim was to provide similar protection a cable would give with its physical barrier to intercept data. Despite these precautions, WEP and the following standards Wi-Fi Protected Access (WPA) and WPA2 were successfully attacked in one way or another.
The very first proposed encryption method (WEP) contained some serious flaws which were already found after some years. As the encryption scheme was inherently broken, it was not possible to fix these issues. Thus, the Wi-Fi Alliance introduced a complete new method in 2002 – the first WPA protocol. It was meant to be a temporary solution that works on older hardware. While releasing WPA, the Wi-Fi Alliance simultaneously worked on a follow-up standard (WPA2) which was released in 2004 to provide a reliable encryption for wireless networks.

WPA2 — properly configured — is still considered generally secure. Even the KRACK attack which received much media attention in 2017 did not reveal a general flaw of the WPA2 mechanism, but an implementation problem in the handshake defined in the standard. A new standard WPA3 is on its way to our devices. It does not reinvent the wheel, but adds new features not present in WPA2. As WPA3 is not widely used yet, we will only talk about WPA2.
WPA2 is mainly divided into two different types, WPA-Personal and WPA-Enterprise. WPA-Personal, also known as WPA-PSK (WPA with a PreShared Key), is considered to be less secure and utilized for private (home) networks. The main threat for WPA-PSK are weak passphrases which are easily cracked by brute-force attacks. At least several hundred passwords can be tested within one second even when using simple consumer hardware. On this basis dictionary attacks are very attractive. To understand, how this would look like, we need to have a look at the four-way handshake.
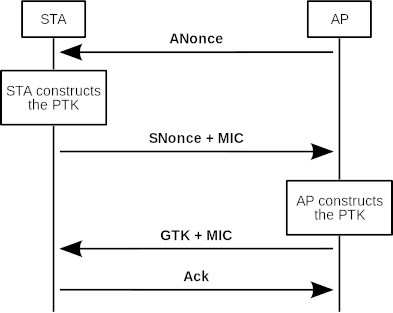
We will not go into detail how exactly the four-way handshake is working as there are good explanations on the web already. But it is important to know that both the client (STA in the figure above) and the AP are creating a session key for their encryption based on a preshared secret and Nonces they are sharing in the four-way handshake. At first the AP is sending a randomly choosen number to the client (ANonce in the figure above). The client is creating a nonce itself (SNonce) and creates a Pairwise Transient Key (PTK) based on the preshared secret, the ANonce and the SNonce. To make it possible that the AP can calculate the PTK as well, the client needs to send the SNonce to the AP. The next messages are already encrypted by the PTK. To make a long story short, after validation not explained here, the client and the AP will accept the PTK as their session key.
Consequently, an attacker can try to brute-force the session key if she has captured the ANonce and the SNonce. The only unknown here is the pre-shared secret and one can try a lot of possible passphrases to calculate the key. This is why the passphrase of a WPA-Personal network needs to be strong and should not be easily guessable. To make things worse, an attacker can try to deauthenticate client and AP (see deauthentication attack below) and thus provoke a new four-way handshake. This is useful if the connection already existed and the attacker was not able to capture the handshake yet.
Apart from the issues concerning weak passphrases the security of WPA-PSK is considered safe in general if a strong passphrase was used. Yet, the encryption can easily be decrypted if an attacker knows the preshared secret. That is the case if you are for example using an encrypted Wi-Fi in a café and it is solely based on a passphrase that is shared with every customer. Anybody knowing this passphrase can decrypt the communication.
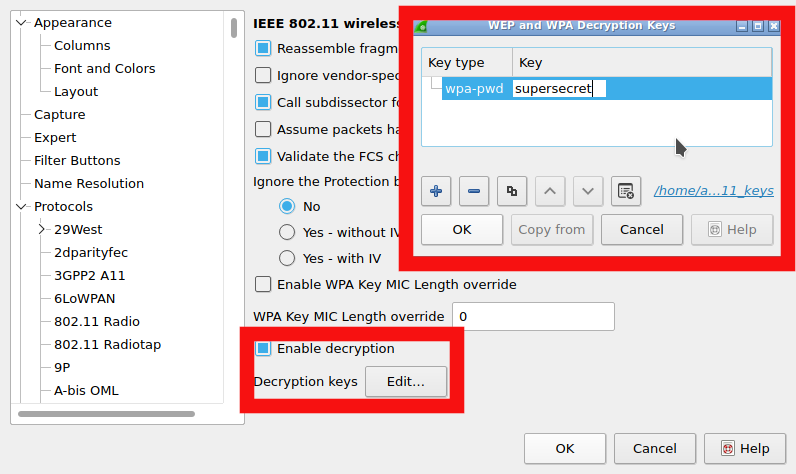
An easy way to do this is using Wireshark. As explained in the previous blogpost your interface needs to be in monitor mode for this to work. If you are now capturing the traffic, you can configure Wireshark to automatically decrypt communication by providing the passphrase (see figure below). Once Wireshark has seen a four-way handshake it will calculate the session key and decrypt all messages automatically.
WPA-Enterprise on the other hand is based on an authentication server and prevents using one single passphrase for access. Instead, individual user credentials are used and authenticated by a RADIUS server that typically operates outside the AP. This feature complicates dictionary attacks or renders them impossible and is therefore preferred in enterprise environments.
In sum most of the known attacks against Wi-Fi encryption are either based on WEP, which is considered insecure for nearly two decades anyway or are based on bad configuration of WPA2 and weak passphrases.
Machine-in-the-Middle Attacks
Machine-in-the-Middle (MitM) attacks form another category of threats against Wi-Fi networks. There are mainly three types of Machine-in-the-Middle (MitM) attacks – Rogue Access Points, Honeypots and Evil Twins.
RogueAP
Rogue Access Points (RogueAP) present a serious danger for networks. Generally the term describes APs, which allow unauthorized access to the network. They can be used with help of an insider e.g. an employee who is intentionally opening such an AP. Publicly accessible rooms are also susceptible for rouge APs. Here, an attacker might place a corresponding device in an unprotected network socket. Likewise a vulnerable or misconfigured AP hijacked by an attacker is considered rouge. As last example recall that enterprise environments usually don't tolerate employee's private hotspots, e.g. via mobile phones. Therefore, these hotspots are regarded rouge as well. Note that depending on the used definition, Honeypots and EvilTwins (see below) may also be referred to as RogueAP.
Honeypots
Honeypots are a convenient way for an attacker to either intrude a client's device or record the network communication of the victim. This kind of attack works, because naive users connect to an unknown open and unprotected AP to get free-of-cost Internet. As the AP is controlled by the attacker she can easily analyze the used connections of the victim. However, in most cases the communication is encrypted on a different layer as TLS encryption becomes a frequently used technique for websites. Nevertheless, the potential for intruding the client's device itself still exist. It should be noted that it is difficult to prevent the establishment of Honeypots within facilities. A good approach to handle this threat is education of users about the risks of connecting to unknown networks. Furthermore, a company may has a policy that prohibits to set up any AP by regular employees (e.g. no APs set up by a smartphone).

EvilTwin
Even so the risk remains that APs which are controlled by an attacker are used to intrude devices and networks. The EvilTwin is an AP which pretends to be a legitimate AP known to the victim. By using the same SSID it appears to be an appropriate Hotspot to connect with. The AP of the attacker may has a stronger signal than any other AP in the environment so that the clients prefer the EvilTwin over the genuine APs. WPA-Enterprise is supposed to minimize/prevent this danger by providing a certificate-based connection that can not be imitated/manipulated by an attacker.
All of these attacks can be achieved by using the famous hostapd software Access Point. It might be far more trivial to set up a "Free Wi-Fi" honeypot than mimicking a legitimate AP though.
Availability Attacks
Availability attacks — often referred to as Denial of Service (DoS) attacks — are used to disrupt the wireless communication. One possible way to achieve is jamming the frequency used by the AP with noise. There is just no way for the AP to prevent this. Luckily, this way of DoS attack is quite expensive. It needs a lot energy and specific equipment to block a frequency with sufficient strength. This kind of attack is furthermore quite easily detectable.
Instead of naive jamming an attacker can execute some simpler and less resource intensive DoS attacks. Most of the 802.11 frames are neither encrypted nor authenticated. This is a security issue as an attacker can easily spoof frames. If there would be a mandatory verification of frames, it would not be possible to execute the following attacks.
Flooding attacks push the stations (STAs, which means either clients or access points) to their limits. Probe request flooding attack for instance would aim at the processing power of an AP. This attack utilizes the feature that an AP has to answer a probe request to be Wi-Fi conform, no matter how many arrive. An attacker just sends as many probe request frames as possible aiming to bring down the AP in its attempt to answer with beacon frames. The same can be done with authentication request frames for non-existing clients. Most flooding attacks are not considered dangerous anymore since the processing power of APs has increased a lot so that they can not be overwhelmed so easily.
Another kind of flooding attack is based on RTS/CTS frames (again, see last blog post for more information). An attacker is able to send these frames without the intention of actually sending data and thus blocking the channel. If done massively, this attack is able to slow down or completely break the connections of the other STAs. Spoofing RTS/CTS frames is easily done as the frames are not authenticated.
Deauthentication/Disassociation attacks are considered the most effective types of DoS attacks on Wi-Fi networks. They are easily executed and have the potential to disturb the entire wireless communication. For this reason, the impact is very high. An attacker just spoofs the MAC address of a STA for a Deauthentication frame which tells the clients/AP that they want to deauthenticate. All involved STAs have to follow this command which consequently results in a disconnection of these STAs. If you like to test you network against Deauthentication attack, you might try mdk3. This tool makes it quite easy to deauthenticate specific clients or even all clients connected to a specific AP.
Fortunately, workgroup `w' of the IEEE 802.11 standard addressed the problem of unprotected management frames by introducing the Robust Management Frames (RMF). By utilizing RMF Deauthentication and Disassociation frames are protected. Now, DoS attacks on basis of Deauthentication/Disassociation are only possible if the Preshared Key is already known. However, Deauthentication attacks are still a threat. Although the IEEE 802.11w standard was included in the standard (currently IEEE 802.11-2017), there are still a lot APs and clients in service which are not able to utilize this version of the specification.
Summary
Attacks against encryption are the most severe one regarding data security. However, they are rather difficult to execute as long as current IEEE 802.11 encryption methods are utilized and configured correctly. MitM attacks are undoubtedly the most threatening attacks as the entire communication can be monitored by the attacker and the security of the network is at stake. Availability attacks are easily performed. Depending on whether network stability is a critical requirement this attack type can range from annoyance to desastrous impacts. These attacks are for sure a severe threat for critical infrastructure which requires wireless Internet access. Nevertheless, industrial WLAN is becoming an interesting topic for companies and is one key element for the so-called "Industry 4.0". This is why we want to have a look at the difference of general-purpose Wi-Fi and industrial Wi-Fi in the next blog post.
Further Reading
- C. Kolias, G. Kambourakis, A. Stavrou, and S. Gritzalis, “Intrusion Detection in 802.11 Networks: Empirical Evaluation of Threats and a Public Dataset,” vol. 18, no. 1, pp. 184–208. IEEE PDF
- KRACK Attacks: Breaking WPA2
- Four-way handshake in WPA
- List of various Wi-Fi tools (a lot of them are for attacking/testing ;-))
